Develop a Cybersecurity Strategy to Prevent Breaches
Why Cybersecurity Strategy is Important?
It’s impossible to ignore the cyber threats in today’s digital age. Constantly evolving technology, threat landscape and consumers cyber awareness can easily overwhelm business and security leaders and fade their focus. Without a clear strategic plan which is aligned with business goals, organization cannot proactively detect and protect its valuable assets, such as client’s data, intellectual property, and reputation from cyber-attacks. Moreover, having a cybersecurity strategy can help organizations comply with increasing regulations requirements.
Additionally, a robust cybersecurity strategy can improve overall efficiency and minimize the impact of cyber incidents on operations, leading the organization to become stronger and more resilient organization. In short, a comprehensive cybersecurity strategy is essential for organization to safeguard its interests and stay ahead of evolving cyber threats.
How To Develop The Strategy That Prevents Next Breach
Without further due, let’s review five steps to develop a sound cybersecurity strategy.
1. Understand the threat landscape.
The first step in developing cybersecurity strategy is defining the organization’s threat landscape. If organization has no threat related to its operations or assets, there is no need to spend resources to protect it. In contrast, without clearly knowing the threats, you can spend resources to protect the wrong asset or get distracted by information buzz.
Defining threat landscape at the start may be overwhelming exercise for less experienced person. Therefore, you can start with the below actions:
- Make a list of threats that are applicable to your organization. Threats should be primarily connected to the business and business environment and can be grouped into accidental, adversarial and environmental threats. e.g., organized criminal group, hacktivists, competitors, employee with privileged access, infrastructure failure, natural disaster, etc.
- Evaluate the threat. You should define the criteria to evaluate threats. e.g.,
- History – did threat materialized during the last 12 months;
- Motivation – is there any motivation to threat to be materialized, or
- Capability – does the threat actor has capabilities to materialize the threat.
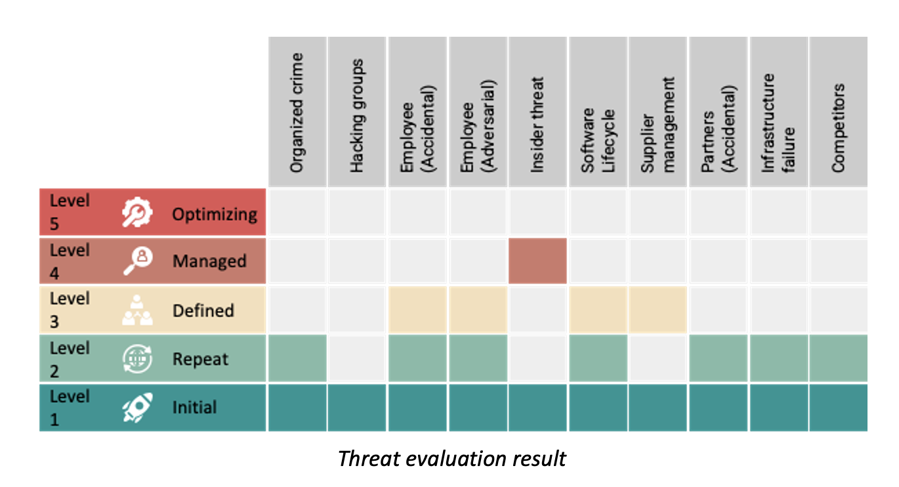
2. Assess your cybersecurity maturity
Once you know your threat landscape, you need to do honest assessment of the organizations capabilities and cybersecurity maturity. You can select one of the widely used frameworks based on type of business and environment, like a NIST Cybersecurity Framework, ISO 27001 or CSA Cloud Controls Matrix. First, assess the maturity of the controls in your organization from design and effectiveness perspective. Assessment should include all IT and security technology.
Then, using the insight from business and the same framework determine where the organization should be in the next three to five years. You need to know about strategic business plans to determine which controls, technology and security processes should be improved. Let’s says the organization will adopt cloud first strategy and all systems will be hosted in the cloud during the next three years. Another strategic plan maybe making workplace fully remote. You need align security strategy with business, so cybersecurity strategy becomes business enabler.
3. Determine cybersecurity strategy
By now, you have established cybersecurity baseline and defined high level goals. In this step, you need to determine tools, processes, technologies, capabilities that you will need. You should also determine how to improve cybersecurity program to achieve your strategic goals. Every improvement requires resources – time, money, experience, etc. Therefore, you will need to design strategic plan in a way to allocate resources optimally, i.e., some changes, processes can be managed with internal resources, some can be outsourced.

Once you have prepared the strategy, the next step is to present it to the organization’s leadership for their review, feedback and “blessing”.
New strategy means introducing new and change existing processes which impacts to the business. Based on leadership awareness on cybersecurity, you can expect multiple discussions before final strategy will be approved.
Hint: Increasing leadership awareness and explaining the strategy’s importance before the formal leadership meeting can help you to buy-in leadership support and commitment.
4. Document and communicate the strategy.
After obtaining leadership approval and commitment, the next step is documenting and communicating the cybersecurity strategy. The strategy is high level document, therefore depending on the audience you will need to develop different versions of it. Senior management and department leaders may need the summary of the strategy to be aware of and support at their level, general staff needs more detailed information, it can be policy or procedure, cybersecurity and IT team may need in a project plan view.
When you write or update policies, procedure, or baseline standards, ensure you involve applicable people and get their feedback. Their involvement helps to better adopt the changes and overall strategy. Another important area is to update cybersecurity awareness materials in alignment with the strategy. This helps to communicate the strategy to the broad audience.

Conclusion
Developing and implementing cybersecurity strategy is an ongoing process and present many challenges. Therefore, it is critically important that you evaluate the organization’s cybersecurity maturity regularly to ensure controls and processes remain aligned to the strategic objectives or identify necessary changes. As early you identify deviations, as more time to correct them. For that, you can engage internal or external audits, or simulate situations like security incident or environmental disaster that help you to identify the maturity of the controls.
Finally, keep in mind that strategy is not set in stone, as organization and external environment changes, you may need to review and align the cybersecurity strategy to the new objectives. Review it, update it communicate it.
If you need a help with identification of the organization’s threat landscape or evaluating current strategy, feel free to contact us. Our experienced professionals will gladly help you in your journey.
